Certifications
CCIO
- Certified Cyber Crime Intervention Officer
CEH
- Certified Ethical Hacker
CISA
- Certified Information Systems Auditor
AZURE
- Microsoft Certified Cybersecurity Architect
AZURE
- Microsoft Certified Azure Solutions Architect
CCNA
- Cisco Certified Network Associate
CCNP
- Cisco Certified Network Professional Enterprise
EAII
- Cisco Certified Specialist
Enterprise Core
- Cisco Certified Specialist
VCP
- VMware Certified Professional Datacenter Virtualization
NCP
- Nutanix Certified Professional Multi Cloud Infrastructure
RHCE
- Redhat Certified Engineer - RHEL
MCP
- Microsoft Certified Azure Administrator Associate
3CX
- 3CX Certified Engineer
NSE
- Fortinet Certified Network Security Associate
My Expertise
• Cyber Security in Medical Devices • Cyber Forensics • Disaster Recovery Planning (DR) • IT
Security • IT Infrastructure Management • IT Services Management
• Business Continuity Planning (BCP) • VoIP Systems • IT Operations Management • IT Project
Management • Hyperconvergence
• Server Management • Virtualization • Collaboration • Network Management • Cyber Forensics
- Having extensive knowledge in penetration testing for applications and
networks,digital forensics, Cybersecurity risk management plan, incident response
plan, and cybersecurity framework.
- Providing expert advice on securing financial technology systems, applications, APIs, and databases, ensuring compliance with industry standards.
- Architect solutions in accordance with security frameworks and policies to protect sensitive data.
- Collaborate with Engineering teams to integrate security best practices in the Software.
- Perform security audits and review penetration tests, presenting actionable reports to leadership and relevant teams.
- Monitor and analyse security alerts and threat intelligence to proactively identify and mitigate security risks.
- Lead security risk assessments and assist with vulnerability management and incident response activities across cloud and on-premise environments.
- Assist investigations into security incidents, perform root cause analysis, and recommend measures for improvement.
- Stay updated on the latest security trends, tools, and regulatory changes affecting the industry.
- Expert in Designing and configuring proof of concept and demonstration environments
for customers include hyper-converged solutions, cloud technologies like Microsoft
Azure and AWS
- Expert in Design and deployment of LAN/MAN/WAN/Wireless networks with Cisco,
Brocade, Fortinet systems and network virtualization (VLAN, VXLAN). Defined and
implemented Network Security, Firewall, VPN, with Cisco ASA/ISR, and intrusion
prevention, Web filtering with Cisco Sourcefire FirePOWER. Built Ixia XGS12/XGS2
BreakingPoint, IIxExplorer IMIX traffic generator, and IxNetwork, IxChariot network
performance tools, and IDS system with Suricata, Barnyard2 and Snorby.
- Expert in Design and deployment of EMC storage (VNX,VMAX,VPLEX,XtreamIO) with
management tools: Ionix ECC, SMC, SRM, SMARTS. Set up EMC CLARiiON, VNX with
Unisphere Manager Domain, MirrorView, SnapView. RecoveryPoint was used for local and
remote data protection. Designed EMC Celerra (NS-120), Centera and CTA FMA archive
system.
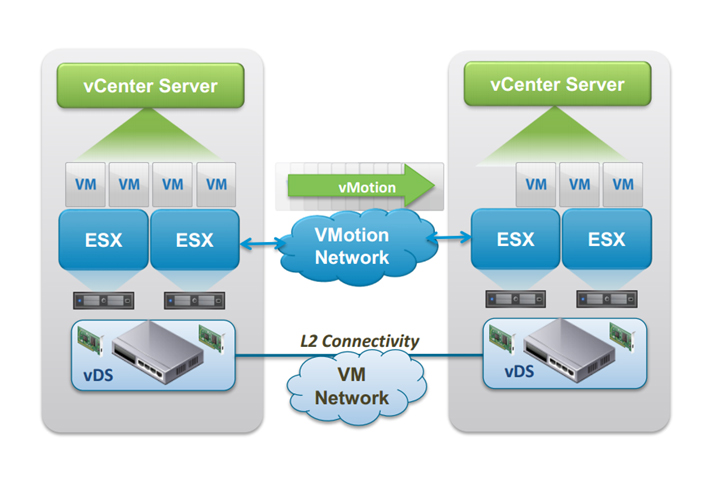
- Expert in designing, installing and implementing VMware ESXi server, VMware virtual
center, setting up V-Motion, HA, DRS etc
- Expert in Design, Deploy, Maintain, upgrade, and implement improvements to the
VMWare ESXi Infrastructure
- Expert in troubleshooting and problem resolution for servers associated with a
VMware infrastructure
- Expert in SAN Architecture, Multipathing, WWNs, iSCSI etc.
- Highly skilled in blade and blade enclosure systems
- Expert in Design and Deployment of High Availability to Microsoft SQL Server
Infrastructure
- Expert in Windows Server 2019 HyperV, Failover Clustering, Network Load Balancing
etc
- Expertise in Active Directory design, migration and support (GPOs,AD
Schema,OUs,LDAP,Sites,Replication,FSMO etc.)
- Expertise in Migration using ADMT migration tool for Active Directory
- Expertise in providing Tier-3 Support for production environments and trouble shoot
critical issues at minimal business impact
- Expertise in Network Security deployment using Cisco, Fortinet and Sonicwall
solutions
- Expert in Design & Deployment of Microsoft Exchange server for multiple domains.
- Expertise in deploying Redhat Linux network infrastructure
- Expertise in deploying Site to Site, Remote Access, SSL VPNs
- Expertise in Designing and Deployment of VoIP call center systems
- Expert in Cisco PIX & ASA Firewalls, Port Address Translation, Identity feature,
Cut-Through proxies, Mail Guard feature, Remote Authentication Dial-In User Service,
Failover capability between primary firewall and redundant firewalls etc.
- Expert in On-Premise to Cloud Migration
- Expert in Microsoft Exchange Server Migration
- Expert in Identifying and mitigating incidents, threats, compromises, and
vulnerabilities
- Expert in Developing standard operating procedures (sops) for network system
security operations and incident response
- Expert in Design and Deployment of VLAN Infrastructure
- Expert in Cisco Routing & Switching Technologies
- Expert in Design and Deployment of SD-WAN
- Expert in Design and Deployment of VoIP Infrastructure
- Expert in Design and Deployment of VLAN Infrastructure
- Certified Cyber Crime Intervention Officer
- Handled many seminars on cyber security and digital transformation
- Trainer for Cyber Security and Networking
- Expert in Design and Deployment of Veeam Backup & Replication
- Expert in Storage to Multiprotocol Environments like CIFS and NFS in NetApp SAN/NAS
environment
- Expert in administering, maintaining and implementing NetApp Storage Systems
Tools & Technologies
• ExtraHOP • Acronis • CipherTRACE • Anomali • Authlogics • MenloSECURITY • DataResolve •
Fidelis • Galaxkey • ZINAD • Armitage • Metaspliotable • Autopsy • WinHex • Pro Data
Recovery
• NMAP • Oxygen • Burp Suite • Splunk • SIFT
• OSForensics • Aid4Mail • HexWorkshop • FTK Imager • Foremost • Scalpel • S-Tool • Registry
Viewer
• USBDView • OWASP ZAP • Recon-ng • Quest Toad • Cisco Packet Tracer • Kali Linux • DEFT •
CAINE • VMWare vSphere • ESXi • VCenter Server • Nutanix Prism • Prism Central • AOS • AHV •
VMware Horizon View • Citrix VDI • Nutanix Frames
Cyber Security Specialties:
• Incident Response, Detection, and Investigations • Security Operations • Cyber Threat
Intelligence • Application, Network, and System Security
• Designing, Deploying and
Securing Web Applications • Darknet Research and Investigations • Source Code Review and Application Security
• Vulnerability Assessment and Penetration testing • System Hardening • IT Security Audits • Cybercrime Investigations • Cyber Security Awareness, Drills and Training • Business Continuity and Disaster Recovery
Current Employment
Co-Founder & Sr. Cyber Security Consultant, Nov 2014 – Present
Sysin Technologies – Calicut, Kerala, India | Doha - Qatar | Dubai - UAE | Dammam -
Saudi Arabia.
Sysin Technologies integrates solutions, designs and builds telecommunications
infrastructures, and provides professional services that increase the productivity of the
Information Technology (IT) departments within enterprises. Focus on deployment of robust
and scalable information infrastructures for businesses of all sizes capable of
accommodating their ever evolving needs. SYSIN, design & deploy leading edge, reliable
solutions for the IT requirements of its clients. This is accomplished by offering a
comprehensive array of networking and telecommunications products mixed with project
management and support services for enterprises and service providers.